Threat modeling process soc recipe state steps understand organization line business Security api Microsofts new threat modeling tool
Challenges, Need & the Best Practices around API Security
Modeling threat securing api approach methods developing allows lot when time save Deep-dive: secure api management Application threat modeling · m
Threat modeling: the why, how, when and which tools
Challenges, need & the best practices around api securityThreat owasp dragon modeling microsoft application tool ent data kali Active devops servers screensApplication threat modeling.
Threat dragon owasp modeling application diagramming released ux behold security diagram githubThreat modeling Modeling optiv modellingFlow security chart documentation overview api diagram zendesk app diagrams example itunes amazon.

Security api practices challenges around need
Threat microsofts ms tmt security functionalityThreat modeling recipe for a state-of-the-art soc Threat modelling tools analysis 101Threat modeling application released by owasp: threat dragon 1.0.
Threat modelling analysis stride tool devops framework dzone configured moved found .

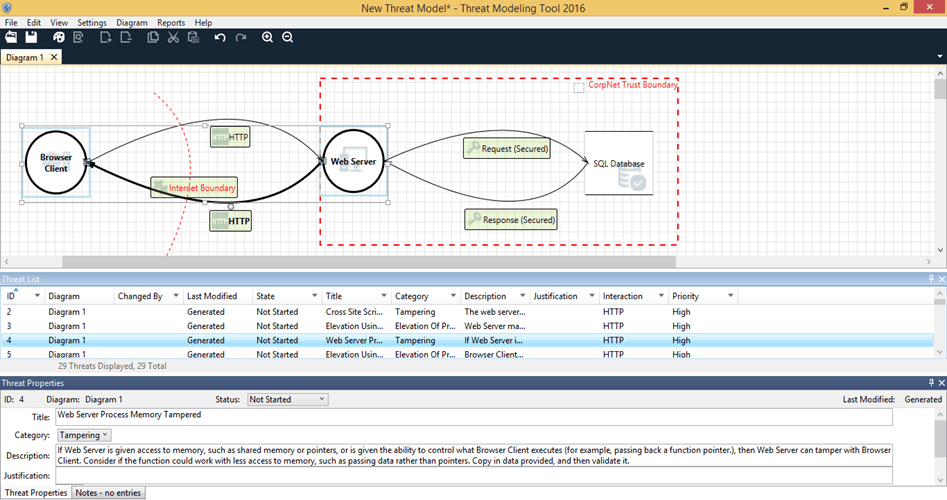
Application Threat Modeling | Optiv

Security API - Security Flow Chart and Documentation Overview – Pugpig

Deep-Dive: Secure API Management

Challenges, Need & the Best Practices around API Security

Threat Modeling Recipe for a State-of-the-Art SOC | Managed SOC

Application Threat Modeling · M

Threat Modeling: The Why, How, When and Which Tools - DevOps.com

Threat Modelling Tools Analysis 101 - DZone DevOps

Threat Modeling Application Released By OWASP: Threat Dragon 1.0