Threat modeling process: basics and purpose Pasta threat modeling Pasta threat modeling
PASTA Threat Modeling - One Day Training - Speaker Deck
Threat attack Threat modeling Myclassnotes: identify threats with pasta
Threat modeling process basics purpose experts exchange figure
Pasta threat modeling method: all you need to knowThreat pasta modeling methodology steps cissp process analysis Threat modeling explained: a process for anticipating cyber attacksAppsec eu 2017 threat modeling with pasta by tony ucedavelez.
Pasta threat modelingPasta threat modeling Threat cybersecurity owaspThreat modeling cyber process sa cso owasp cc diagram data flow anticipating attacks explained online banking idg.

Pasta threat modeling for cybersecurity
Practical threat modeling series, part 4Threat simulation modeling Threat pasta modeling training data diagramming dfds architectural flow elementsPasta threat modeling methodology training defines attack surface important.
.


PASTA Threat Modeling Method: All You Need to Know - RCyberSolutions.com

Threat Modeling - ITperfection - Network Security

AppSec EU 2017 Threat Modeling with PASTA by Tony UcedaVelez - YouTube

Practical Threat Modeling series, part 4 - Waterfall Vs Agile

PASTA Threat Modeling - One Day Training - Speaker Deck
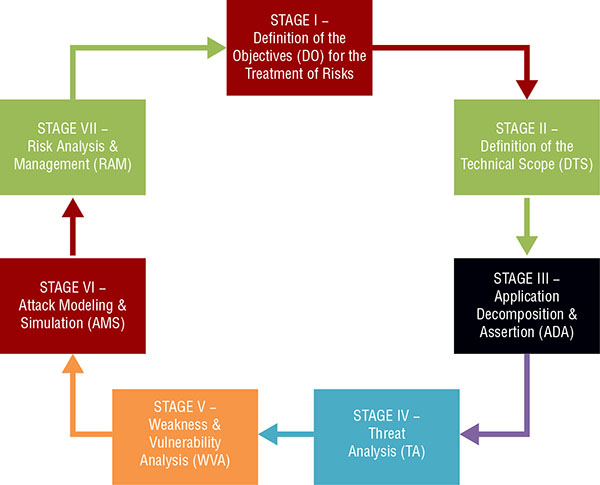
MyClassNotes: Identify Threats with PASTA

Threat modeling explained: A process for anticipating cyber attacks

PASTA Threat Modeling for Cybersecurity | OWASP All Chapters 2020

PASTA Threat Modeling - One Day Training - Speaker Deck